Once upon a time, a company’s operational boundaries were clear and stable. In operational terms, the enterprise could be conceived of as the sum of its headquarters, satellite offices and perhaps the physical locations of premium partners. Employees and partners connected with each other in person, or via secure telephone lines, or via secure desktop computers.
Today we live in a different world. Enterprise boundaries have become wider, fuzzier, and more fluid. More employees work remotely than ever before. Employees are asked to BYOD — bring your own device. Partners and suppliers have become more plugged in; they too have their devices. And beyond people-to-people communications, the Internet of Things (IoT) has shepherded in an era of sensors everywhere. Data from the edge streams into rivers that pour into enterprise data lakes. Today that data may originate from customers, competitors, partners and prospects — but also from “things” such as RFID tags on animals, or sensors that measure perimeters, ovens, chemicals and a vast array of other use cases.
Two emerging trends — the rise of sensors and the mobile workplace — increase the sentience of the enterprise. People and devices sense, send and respond. They are “In The Loop” (powered by a rich diversity of feedback loops). But despite the obvious benefits of a connected enterprise, risks abound. For the hyper-connected enterprise, security and privacy become significant technical challenges. It takes smart technical design and continuous vigilance to maintain the security and trust of all enterprise stakeholders.
In this chapter I will touch on:
- IoT and mobility: the background
- Uses
- Technical building blocks
- Implications for the fit systems enterprise
IoT and Mobility: Background
It began with a Coke machine in the corner of the Computer Science department at Carnegie Mellon University around 1980. The department had expanded. The desk-to-Coke-machine distance had increased for many, creating a problem. Too often, a caffeine-starved programmer would make the trek to the machine, only to find it empty — or that their Coke, just recently restocked, was still warm. So a couple of programmers installed micro-switches in the machine and hooked them up to the internal computer network. Now a programmer could check on the Coke machine’s status (EMPTY, WARM or COLD) before exerting the energy to walk over to the machine. In time, improvements were made so that the machine could be queried on ARPANET (precursor to the Internet), enabling people in other buildings (and for that matter, anywhere in the world) to know the Coke machine’s status.
It was the world’s first known IoT application.
Today, IoT is transforming every industry and every aspect of life on earth. From smart buildings to smart cities to smart cars and smart highways, IoT powers intelligence:
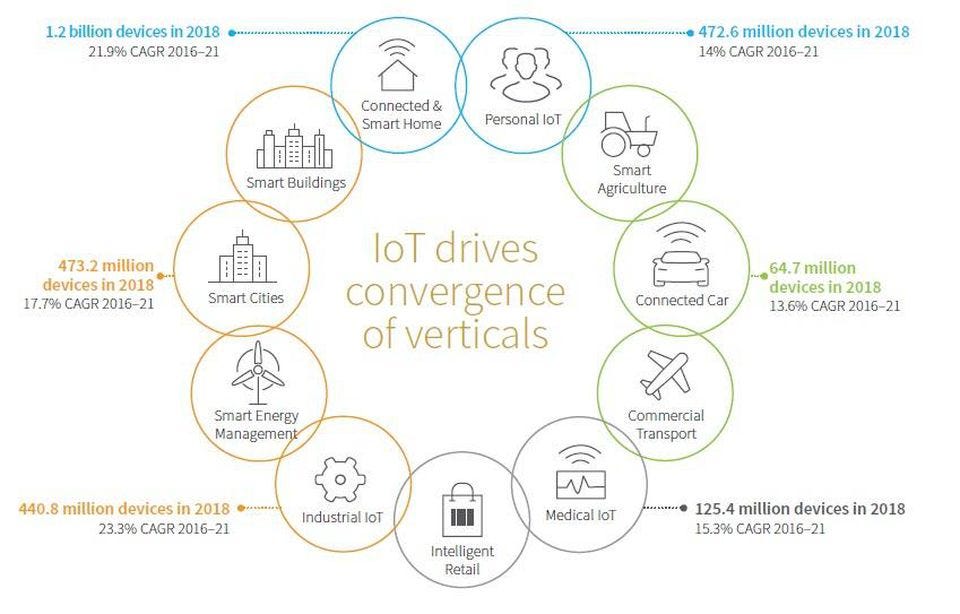
The number of IoT devices in the world today is double the world’s population. By 2030 it is estimated the number will be 125 billion — fifteen times the world’s population. IoT and mobility stand alongside AI, machine learning and cloud computing as essential drivers of change in today’s digital era. For the fit systems enterprise, IoT is likely to play a significant role in products or processes — whether through home grown or vendor-provided solutions.
Statista.com is another research firm that projects a rising adoption curve:
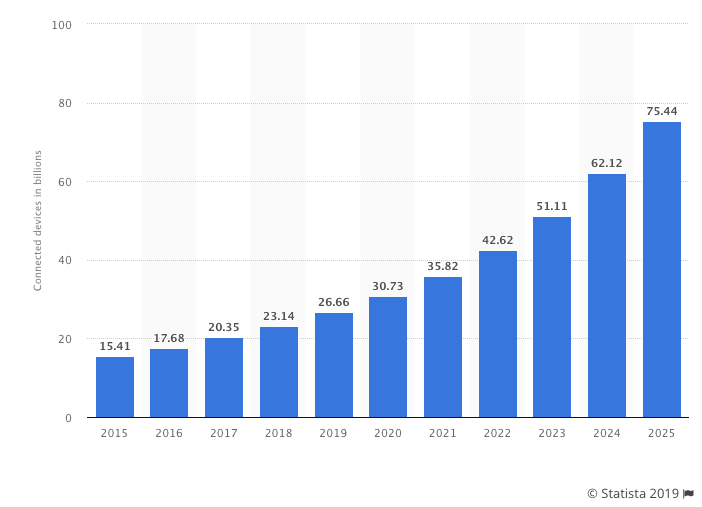
McKinsey & Company believes the overall impact of IoT on the worldwide economy will reach $11.1 trillion by 2025¹.
So what is IoT?
An IoT solution connects machines, physical devices, everyday objects, animals or people (tagged with unique identifiers) to the Internet, enabling transmission of data into edge-based and / or central systems for analysis and response. This requires endpoint sensors and actuators, communication networks and enterprise data processing engines.
The IoT explosion has been sparked by a convergence of technology developments. These include smart sensors at the edge; edge computing; modern networking; massively scalable, cloud-based fast data platforms (built via reactive microservices architecture) that can handle real-time streaming data; and associated advances in big data analytics, AI, machine learning and deep learning.
It all starts with an endpoint. The endpoint exists to sense something (active), or be sensed by something (passive). Its purpose might be to sense a plume of toxic gas emerging from a chemical plant. For this purpose, a WiFi-enabled sensor might send alerts back to a central point. Or it might be a truck in a fleet that needs to be tracked: here GPS and cellular technology combine. Or perhaps there is a passive RFID tag or label attached to a chair in inventory. Such a tag would be read by an RFID reader, which would send the data to a middleware solution, perhaps for real-time edge computing, before sending prioritized data on to a central system. To do their jobs end points must have a power source, a communication method, and an IP address with a unique identifier.
To pursue your IoT agenda, a variety of vendors are there to help. The job of any vendor solution is to abstract away a problem you would otherwise need to deal with yourself. Vendors sell sensors, actuators, control platforms, edge computing solutions, networking solutions, databases and any number of cloud management platforms. Wherever a vendor tool does the job, it’s probably the simplest and best way to go. Wherever you find that off the shelf solutions don’t serve your need you’ll have no other choice than to build it yourself.
An important subset of IoT is enterprise mobility. In today’s enterprise employees and partners access enterprise data and engage in business communications through personal devices. The same security and privacy issues encountered with IoT apply to enterprise mobility.
Uses
IoT has emerged to serve a rich diversity of consumer and industrial applications. Broadly speaking, these applications fall into three categories:
- People to people (enterprise mobility: Zoom, Slack, email, enterprise apps)
- Things to systems to people (monitoring, analytics and response)
- Things to systems (robotic process automation, cognitive systems)
Enterprise Mobility
Gallup reported in 2017 that 43% of American workers work remotely at least part time. In fact, the ability to work remotely is seen as a major factor both in job selection decisions and in job satisfaction.
Enterprise mobility starts with BYOD. Employees connect to the enterprise via their personal computers, smartphones, tablets and watches. And it’s not just email and calendar anymore. They connect in Zoom conference calls, Slack sessions, and inside enterprise mobile apps.
Needless to say, the primary issue faced by the enterprise is security. Some of the largest and most technically sophisticated companies on the planet have been breached (including Yahoo — 3 million records; Facebook — 500 million records; eBay — 145 million records; and JP Morgan Chase — 85 million records). Often, system access is achieved by tricking employees into sharing their login credentials or gaining unauthorized access to employee personal devices for use as stalking horses.
Enterprise infrastructure and DataOps teams need to build systems and security protocols that close these security gaps while retaining remote access. This requires an enterprise mobility management strategy. Such a strategy brings together five management domains:
- Mobile device management
- Mobile email management
- Mobile content management
- Mobile application management
- Mobile endpoint management
There is more to read about this subject in Chapter 29 — Trust.
Things to Systems to People
In the consumer world, IoT is all around us. It has emerged in personal devices, smart home voice hubs, smart appliances, smart cars and smart retail experiences. Fitbit and Apple Watch record your exercise progress and heart health. Go to DisneyWorld, and you will wear an RFID-enabled Magic Band. Google Home and Amazon Echo whisper an answer in your ear to every request. In the home, appliances such as refrigerators and dishwashers, HVAC control systems like Nest and security camera-enabled doorbells like Ring provide alerts and maintain control via the Internet.

A wide array of industrial applications has also emerged. Deloitte projects the number of devices and dollars spent by 2020 by sector as follows (CAGR since 2014 in brackets):
- Manufacturing: 680 million devices (13%) / $136 billion (9%)
- Auto: 740 million devices (83%) / $303 billion (51%)
- Agriculture: 30 million devices (35%) / $25 billion (15%)
- Retail: 400 million devices (54%) / $13 billion (9%)
- Health care: 130 million devices (22%) / $25.5 billion (16%)
- Transportation and Logistics: 370 million devices (18%) / $491 billion (9%)²
Things to Systems
For many applications, sensing and response occurs without direct human engagement. The autonomous vehicle automatically adjusts to objects on the road. The robot makes its way around the warehouse, moving things in a sequence defined by rules. Humans monitor these systems, but their operational actions do not require human engagement.
Take Arby’s Restaurant Group. The company had a problem. Despite sales growth, rising operational costs were causing profit growth to fall behind. Since sales were already rising, the company couldn’t count on further sales acceleration to solve the problem. It needed to increase profits without raising prices, reducing the amount of meat in their sandwiches or other tricks that hurt their customers.
Arby’s management began to look at the costs being driven by aging stores and equipment. HVAC equipment, refrigerators and stoves were driving up costs in operations and repairs. In 2013, Arby’s brought in the SiteSage platform, provided by Powerhouse Dynamics, as an IoT platform to monitor and control HVAC units in its 1000 restaurants. The system provided alerts on the status of HVAC systems, leading to significant improvements in maintenance and repair — and a significant reduction in costs. This first IoT project significantly contributed to a 15% reduction in the company’s energy costs by 2015.
Since that first IoT initiative, Arby’s has gone on to install sensors in refrigerators and stoves. Data from refrigerators ensures cooling failures can be identified and fixed before food spoils. Data from stove use is leveraged to improve worker training, such as keeping stove doors closed to avoid heat loss. IoT is now being used to control food safety from the beginning of the supply chain through to its presentation to the customer³.
Where it’s Headed
We are just at the beginning of IoT penetration and adoption. SRI projects that the miniaturization of devices, more power-efficient electronics and 5G will support rapid expansion of IoT. We are already in a world where distant objects can be controlled as well as monitored.
Competing technologies envision different futures. Some companies are working towards a world where the IoT platforms and gateways will be abstracted away, replaced by simple, secure, low-cost networking solutions executing at the root of the network — the TCP/IP level. Other companies are doubling down on the platform / gateway, continuously adding business logic to serve new use case permutations. In the future, expect to see the data from disparate sensors and systems merged together to deliver more nuanced and multidimensional insights. This has been called advanced sensor fusion.
Technical building blocks
An IoT system is made up of three domains: the edge, the platform / gateway and the enterprise data analysis system.
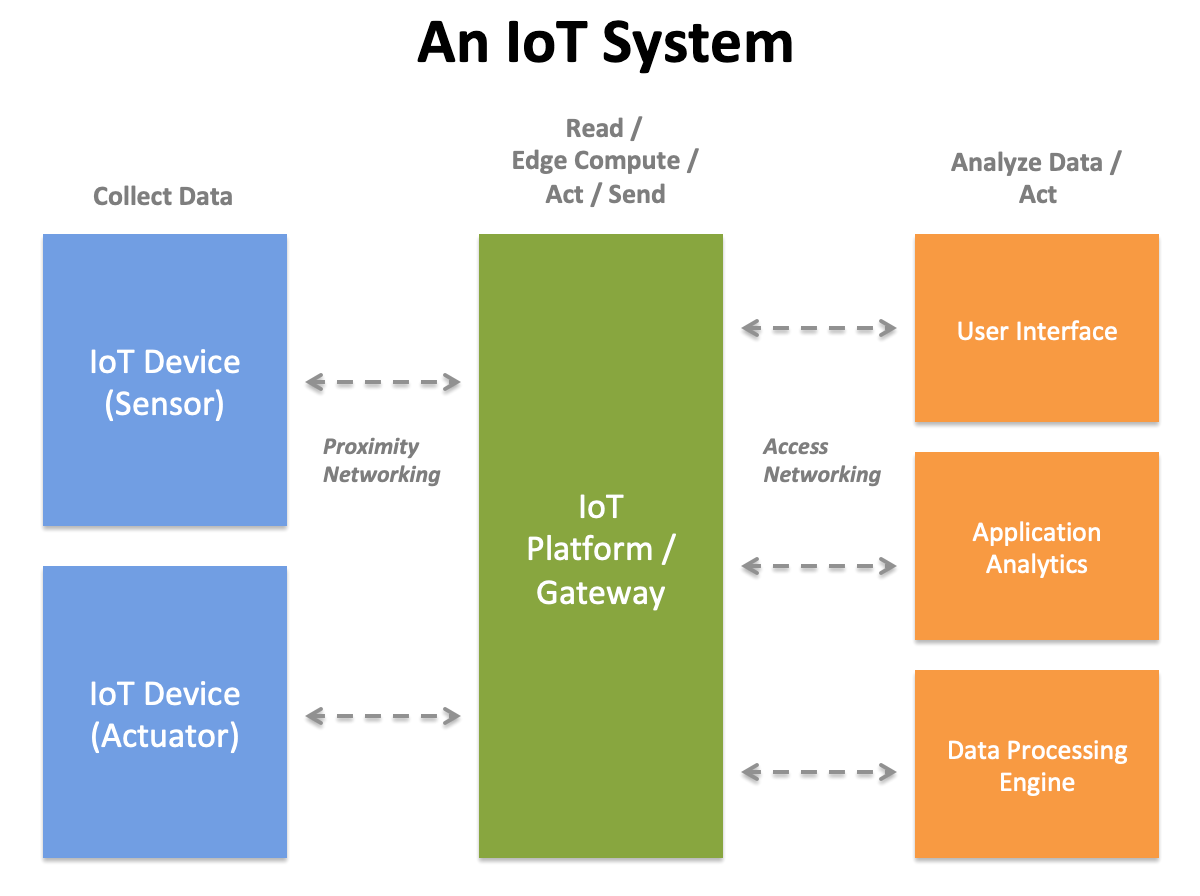
Overview
IoT applications drive high variety, velocity and volume of data. This data must be ingested, stored, queried and acted upon efficiently and securely. Sensors and actuators at the edge can be vulnerable to penetration, in the same way that employee smartphones can be enterprise vulnerability points. And faulty IoT applications can lead to dangerous conditions: such excessive heat in an oven, an undetected hazardous chemical release, or an autonomous car driving into a brick wall. Specific requirements will depend on the application, but issues of latency, cost, security, failure detection, health checks and accessibility must be dealt with in system architecture.
Enterprise system architecture considerations will include:
- Choosing the right edge device for each job — considering factors such as data streaming requirements, range, power requirements, device life, device cost, and need (sensing only vs. sensing plus actuating)
- Capacity for edge device detection, health check and authentication: devices are hardware; they can fail, be stolen or be tampered with
- Capacity to configure actuator controls
- Capacity to manage network traffic, such as through SDN
- Capacity to tier data — processing data at the edge for real-time applications, and moving data to the enterprise for analysis
- Capacity to combine diverse IoT applications into an integrated system, such as for a supply chain solution (truck movement, pallet movement, temperature checking and inventory control)
- Capacity to integrate the data from diverse IoT applications into a comprehensive data analysis
- Capacity to test the interactions between diverse IoT applications so as to detect unintended events
- Ensuring security in depth throughout the system from end points through edge devices and networks into the enterprise
- Designing for obsolescence and replacement
- Designing to avoid vendor silos and enable inculcation of emerging technologies
The Edge
What are you trying to do? Sensors sense things. Actuators do things.
Perhaps you want Internet enabled security cameras to create a video record of a physical space. Or you want to detect force, load, motion, torque or tilt. Or track acceleration, velocity, strain, flow or pressure. Discover leaks, levels, humidity, moisture or displacement. Recognize sound, vibration, ambient light or dimensions. Calculate temperature, magnetic force or voltage. Discover the presence of chemicals or gases. Observe digital, human or vehicular traffic. Sense penetration of a perimeter. The applications for sensors are many.
Once you have sensed a thing, you may want to do something. If you simply want to analyze sensed data, then a sensor will suffice. But you may need to take immediate action such as to activate a lever, or sound an alarm, or initiate a video recording, or release a chemical, or increase the temperature, or turn off the washing machine, or turn off the lights. For actions such as these you will need an actuator.
If the edge objective is simply to sense and send data, then a passive RFID tag may be sufficient. Applications such as inventory control and building access control fit this use case. A thin, printable tag chip features an antenna. The antenna picks up the radio waves emitted by an RFID reader, using the reader’s energy to power the tag (so that it doesn’t need a battery). Passive RFIDs are inexpensive and can be read at a fast rate. However, the reading range is short. If it uses low frequency radio waves, the reader will need to pass within one or two feet of the tag. An example is a building access key. If the tag uses high frequency, it will be able to pass within a few yards, making it useful for such things as the tracking of library books and pharmaceuticals. If it uses ultra high frequency it can be as far away as 100 yards or more, which works for other types of inventory control, asset management, patient tracking and events management.
An active RFID device is more elaborate. It has a battery incorporated into a surface-mount device, so its form factor is more substantial. On a regular interval, an active RFID device will emit a radio frequency chirp, which can be detected by a reading device. Because there is a transmitter within the tag, the signal can bounce off surrounding walls and materials, extending its range to multiple hundreds of yards. Active RFID devices are used to track high value assets such as pallets and shipping containers. Because active RFID devices include a battery, they can also contain sensors that measure such things as shock, temperature or humidity.
Bluetooth Low Energy (BLE) sensors are similar to active RFID devices, but are easier to combine into a whole system. That’s because BLE can communicate with other sensors and laptops, tablets and smartphones, and can easily be uploaded to cloud-based systems. Systems for health care, sports and fitness, light monitoring and other applications work well with BLE.
You may need to incorporate GPS into the edge device, if your application requires mobile geolocation. You’ll tap into cellular networks — either narrowband (NB-IoT) or Category M1 (Cat-M1 IoT). NB-IoT has a much smaller bandwidth, resulting in lower transmission power. Cat-M1 can deliver much higher data rates. Both provide a long data range — 50 miles or more. So GPS needs to be deployed inside cellular IoT hardware.
The challenge is that GPS is inherently a power hog. GPS requires at least four satellite signals to plot the location. It needs to constantly search out satellites in order to provide real-time geolocation. So if the device is not connected to power its battery will need to be relatively big, and battery life will be relatively short. Both these factors make the device more expensive than other types of edge devices. One strength of cellular IoT hardware is that it can access the existing cellular infrastructure for networking. In most parts of the world, its range is substantial: as far as the installed cellular infrastructure allows. For this reason it’s likely to be more reliable than its unlicensed counterpart, LPWAN. However, if reliability and range requirements are low enough, LPWAN may be a cheaper and easier-to-maintain alternative. The range for LPWAN solutions is about five miles.
Actuators react to the data streaming in from sensors, either within the device itself, or via commands returning from the platform / gateway, or via commands from the enterprise system itself. An actuator is a microcontroller — a system on a chip built to execute simple jobs at the edge. It may be used to regulate any system in response to sensor data — such as to increase or decrease the temperature, or shut off the water, or set off an alarm. Smart locks, smart power outlets and door controls are examples of actuators. Examples of control platforms that direct actuators include Amazon’s Alexa, Apple’s HomeKit and Samsung’s SmartThings.
The Platform / Gateway
Data is gathered from the edge through readers. These readers are part of the middle layer of IoT architecture. Depending on the application, the reader may be smart or dumb. It may simply transmit data between the edge and the enterprise data analysis system, or it may do work in between.
This is an important consideration. If your use case allows, it is best for edge data to arrive at the enterprise with minimum business logic transformation. For instance, with peer to peer connections, technology now exists to enable the data to pass without even going through the vendor’s server (once the connection has been initialized on the cloud). This makes it more secure, faster, lower cost, less prone to failure, “always on” with no timeouts, and continuously addressable (since the connection address stays constant). If your application requires that you establish a cloud proxy, then the URL and port addresses will change every time you connect, and you the system will need to be set up with time outs so that compute power isn’t tied up indefinitely. If your application requires significant business logic transformation in between the edge and the enterprise, you will add further complexity.
The general principle is “simple is better.” The more complexity you introduce, the more technical support (and cost) will be required to maintain the system.
When it’s important to act in real time on sensed data, processing needs to occur close to the edge. With an autonomous vehicle, the processing needs to happen within the car. With other applications, the processing may need to occur within a few miles, so as to ensure minimum latency. With edge (or fog) computing, data is stored in microcenters for local processing. Aggregating data locally reduces latency and saves money. You can tier your data, acting on data as necessary close to the edge and then pushing a subset of the data up to the enterprise data analysis system.
All of this data movement requires connectivity, which is achieved through the access network.
Because of the diversity of IoT applications that an enterprise may employ, and the desire to integrate the data, it may be helpful to adopt a network architectural style called Software Defined Networking (SDN). With SDN, the network control and forwarding functions are decoupled. This ensures that network control can be programmable. The OpenFlow protocol can be used in SDN. SDN is:
- Directly programmable
- Agile (by abstracting control from forwarding, administrators can dynamically adjust network traffic from endpoint through the entire system)
- Centrally managed (SDN controllers maintain a global network view)
- Programmatically configured (automated programs can configure, manage, optimize and secure network resources
- Open standards-based and vendor neutral (simpler network design because instructions provided by SDN controllers you can write yourself vs. depending on vendors to deal with multi-device complexity)⁴
Connectivity options are shown below:
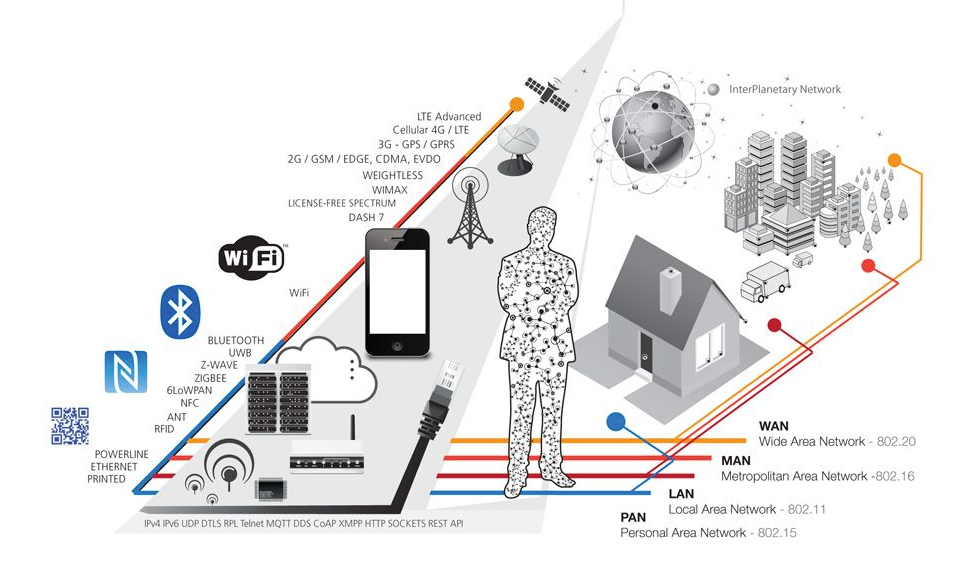
Connectivity can be achieved via short range wireless (such as Bluetooth Low Energy, Near Field Communications, LiFi and WiFi), medium-range wireless (such as LTE-Advanced), long-range wireless (such as LPWAN and VSAT) and wired (such as via Ethernet and power lines).
The Enterprise Data Analysis System
To leverage the data that streams in from IoT solutions, you need enterprise technical systems built via reactive microservices architecture, leveraging cloud-based distributed computing(Chapter 24). The data can be processed and analyzed as big data (Chapter 25), or via AI, machine learning and deep learning methods (Chapter 26).
Emerging Technologies
5G is on the horizon. It is likely to lead to a significant expansion of cellular-based IoT applications. While 4G can only support 4000 devices per square kilometer, 5G will be able to support 1 million. Low power, low cost devices will be able to connect at scale with low-latency communications. Speed will be slightly higher than 4G; under the ultra-reliable low latency communication standard it will be 1 millisecond; under the enhanced mobile broadband standard it will be 4 milliseconds. Industrial and consumer IoT applications will become more reliable, faster and cheaper due to 5G.
Nanotechnology will also impact IoT. Sensors will become smaller, enabling new applications (such as with medical implants). It will also enable faster processing and cheaper storage. Transistors, solar cells, light emitting diodes and diode lasers will all benefit from advancements in nanotechnology.
Implications for the Fit Systems Enterprise
The primary building block of the fit systems enterprise is the feedback loop. Leaders become In The Loop because they have access to the data necessary to make smart decisions. For many companies, IoT and enterprise mobility make them more adaptive. The adaptive enterprise is resilient, scalable and efficient. For some, IoT will directly increase customer value — i.e. make the enterprise more generative.
In the old days, the enterprise was, from a technical perspective, a closed system. Today all enterprises are open systems. In a world where enterprise boundaries have become wider, fuzzier, and more fluid, the missions of the engineering system and the DataOps system become much more challenging. As the number of moving parts and entry points into the enterprise grow, issues of privacy and security will predominate. These issues are both technical and ethical. That’s why it is so important for the In The Loop leader to be an ethically grounded, digitally literate systems thinker.
To view all chapters go here.
If you would like more CEO insights into scaling your revenue engine and building a high-growth tech company, please visit us at CEOQuest.com, and follow us on LinkedIn, Twitter, and YouTube.
Notes
- “What Is Internet of Things (IoT)? — Definition from WhatIs.com.” IoT Agenda, n.d. https://internetofthingsagenda.techtarget.com/definition/Internet-of-Things-IoT.
- “Harnessing the Power of Internet of Things to Transform Industry in India.” Harnessing the Power of Internet of Things to Transform Industry in India. Deloitte, n.d. https://www2.deloitte.com/content/dam/Deloitte/in/Documents/manufacturing/in-mfg-harnessing-the-power-noexp.pdf.
- Moore, John. “IoT: Food Service Industry Meets Technology in Arby’s Deployment.” IoT Agenda, July 29, 2016. https://internetofthingsagenda.techtarget.com/feature/IoT-Food-service-industry-meets-technology-in-Arbys-deployment.
- “Software-Defined Networking (SDN) Definition.” Open Networking Foundation. ONF, n.d. https://www.opennetworking.org/sdn-definition/.

